
Photo: Harland Quarrington/MOD



Photo: Sgt Tom Robinson RLC/MOD
In 2023, every organisation and every person is touched or influenced by technology, even those who may not actively seek to participate, such as those who consider themselves as technophobes or a digital minimalist.
Regardless, from a Cyber Attackers perspective, all are legitimate targets to exploit.

360 Defence (360D) are at the forefront of leading on Cyber Security and Cyber Defence in the UK and internationally for over two decades.
Our specialist approach is to think worse than the attackers and consider any viewed mission, service, asset, programme or project in a real world context of what damage the threat sources can inflict on you and equally how interested are they in you.
We help clients defend themselves with real world approaches by applying a proven common sense, targeted approach building from a basic solid foundation using a simple service catalogue.
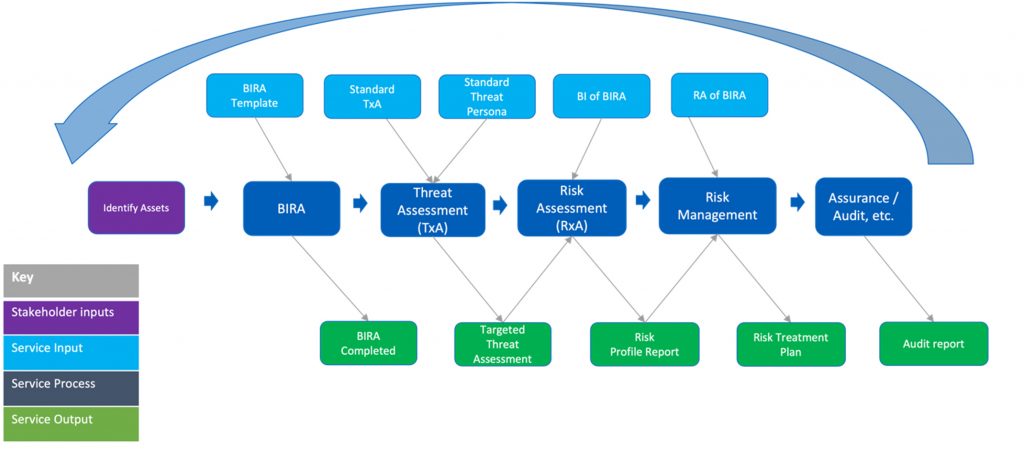
The above includes:
- Assets to be protected.
Our work includes defining those for clients as required. - BIRA
- Threat Assessment (TxA)
- Risk Assessment (RxA)
- Risk Management (RxM)
- Assurance/Audit (AnA)
e.g. ensure that the security risk management countermeasures are working and managing risks as expected.
BIRA
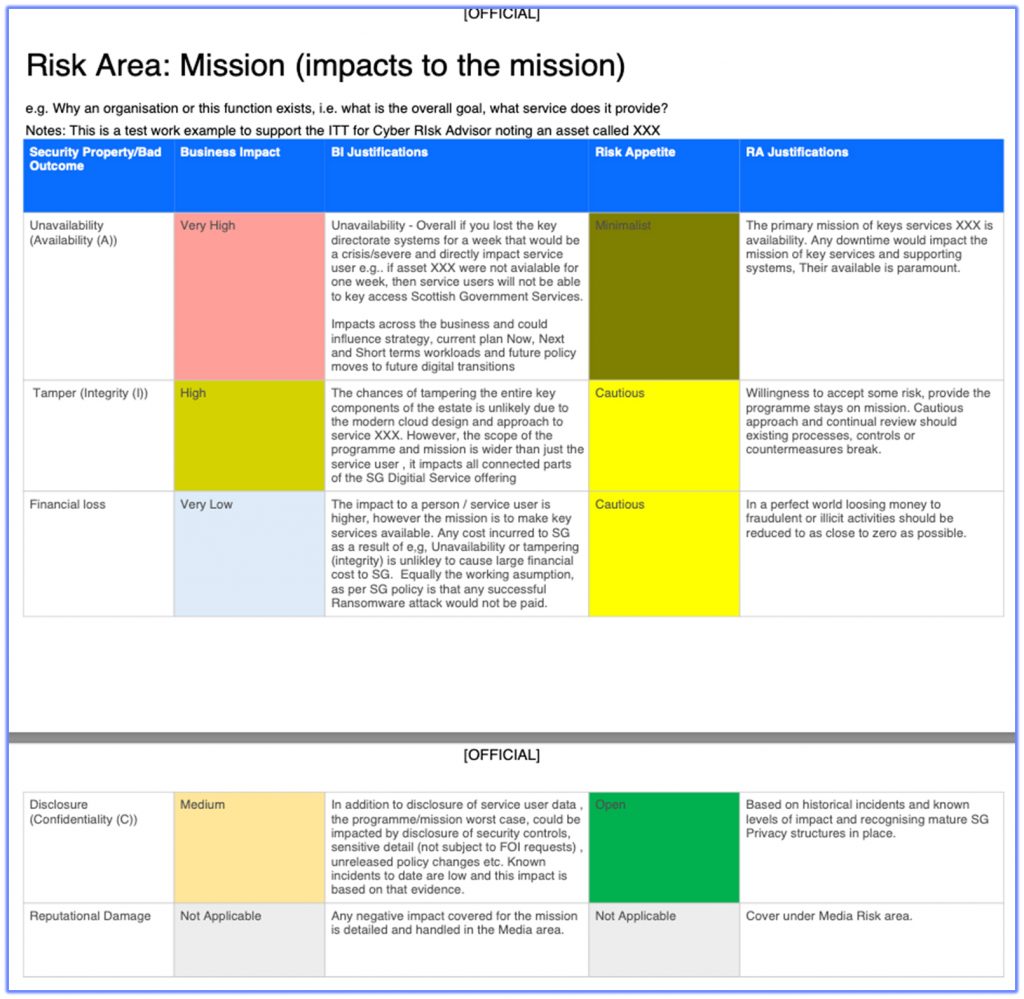
360D with partner designed Business Impact (BI) and Risk Appetite (RA) short assessment can be run at a macro or micro-level. (Asset/target dependant)
BIRA (Hosted by friends at 2T) gives inductive impacts against bad outcomes and the appetites that the business has with regards to those bad outcomes such as Disclosure (Confidentiality) Breach, Tampering (Integrity) Unavailability (Availability) , Financial Loss, Reputational Damage etc.,
BI considers a worst case scenario, whilst striking a balance between plausibility, likelihood and hindsight so that realistic and importantly, manageable Business Impacts are agreed. This inputs into Risk Assessments (RxA)
RA is the business process to assess the level of risks that are acceptable vs unacceptable and those that exceed the appetite need to be risk management (RxM)
Threat Assessment (TxA)
360D Specialism ranging from a light, mid or full touch presented in either traditional Capability and Motivation (of attackers) or in (Intelligence based) PHIA Yardstick terms .
Fuller touches can include a managed OSINT deployed containerised platform capability to research and collect high value intelligence anonymously and securely without detection e.g., What is the increased risk of opening a new business operation in Country X considering the current geo-political situation and what do the threat sources know of my organisation or product.
TxA is a targeted report and can include AI generated threat Personas (if applicable) e.g.,
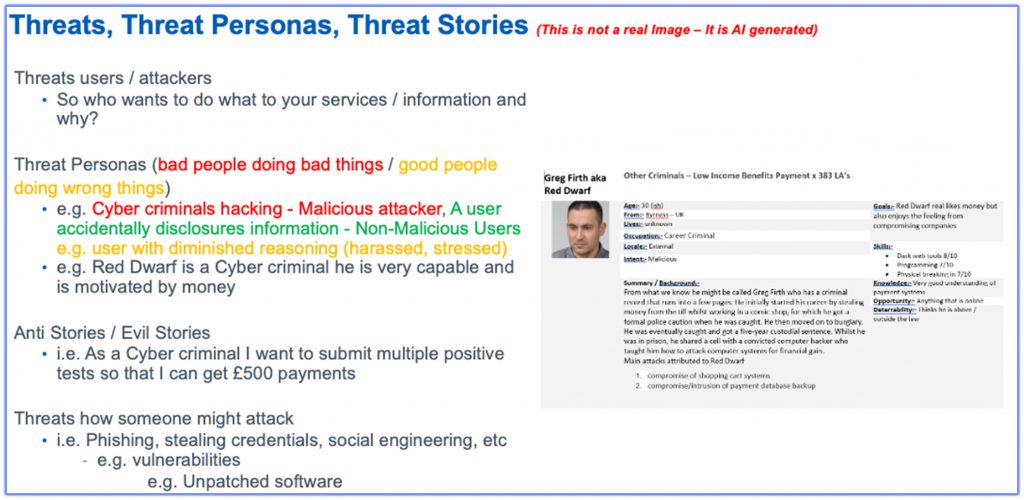
TxA feeds Risk Assessment (RxA)
Risk Assessment (RxA)
Risk Assessment (RxA) including Threat Modelling (TxM) – 360D Lead specialism.
RxA is the process to identify specific risks to a target (for example building, person, process, technology etc.) based on threats, likelihood and business impacts.
Example methodologies:
- Threat Modelling (STRIDE, DREAD, etc.)
- Mitre ATT&CK (https://attack.mitre.org/)
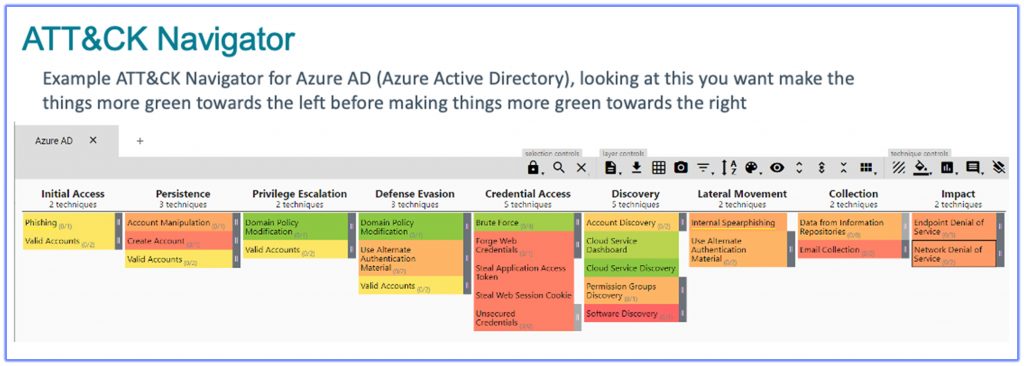
Including 360D and partner designed RiskBlox (hosted by friends 2T Security)
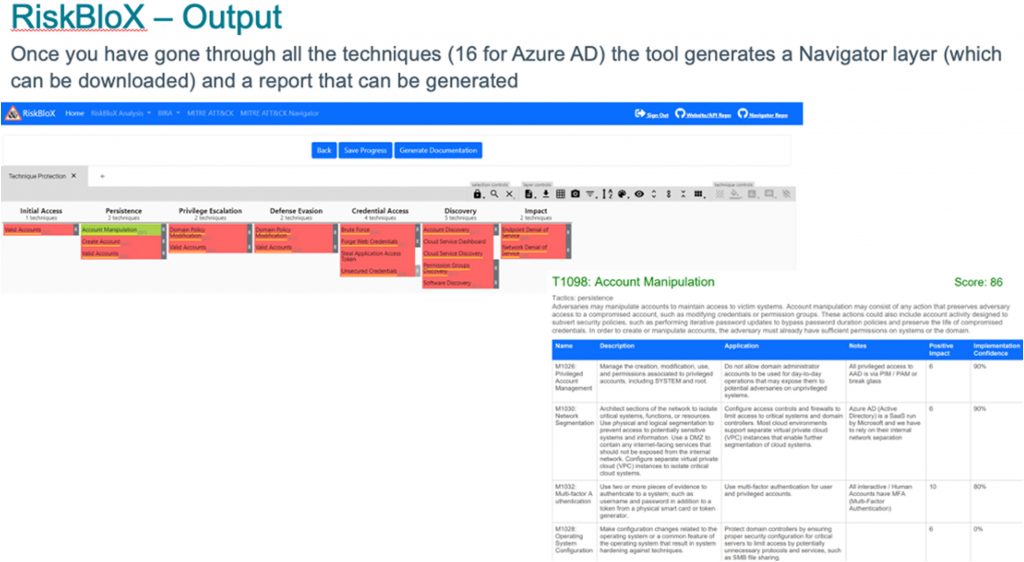
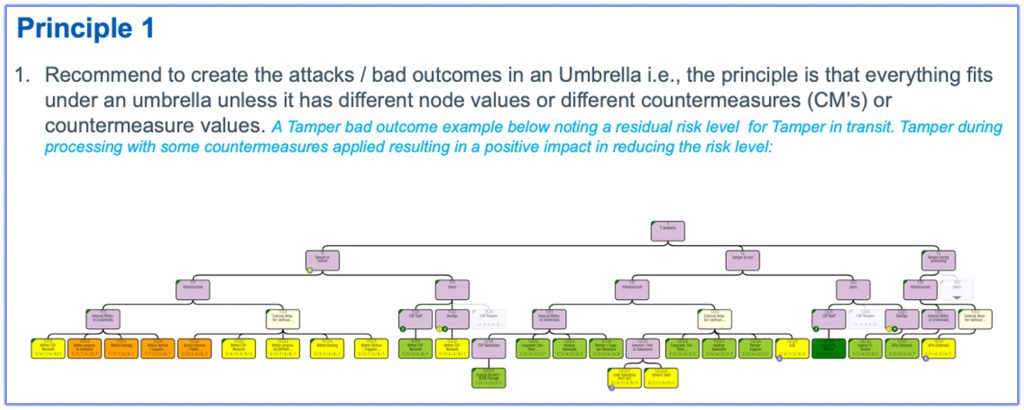
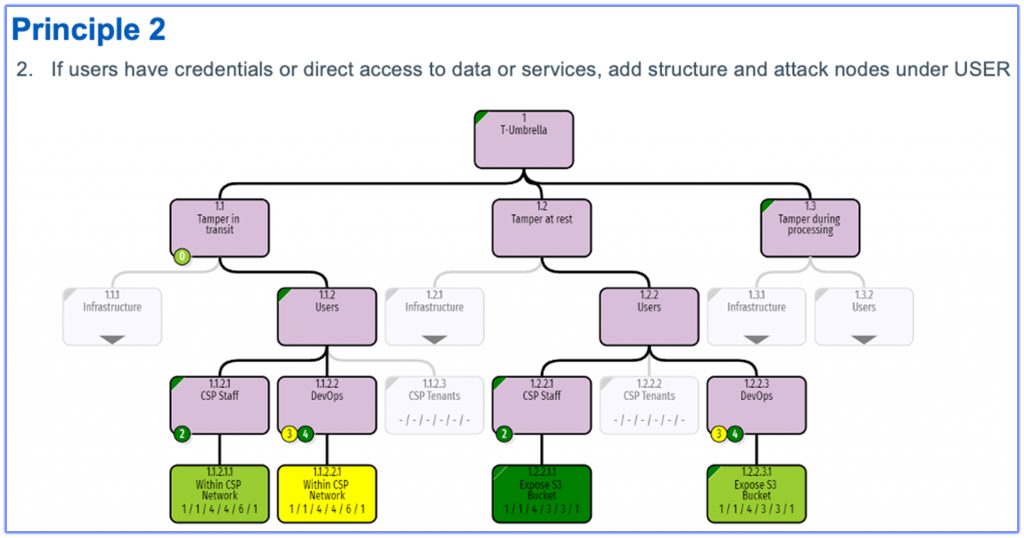
Attack Trees (RiskTree™) 360D examples below including the application of some suggested principals.

Risk gap analysis (for example against NCSC Cloud Security Principles, CSA STAR CMM, etc.)
Risk Management (RxM)
Security Risk Management make and record identified risks in the central risk register, support to assess changes to impact and likelihood, plan mitigations and track the risk throughout the lifecycle e.g,. Risk Treatment Plan (RTP) of the risks discussed with the risk owner what needs address by when and how. (Product Owned)
- Updates/additions into Organisation (Single) Owned Risk Register (various organisations have differing views for example add all identified risk vs just those risks above appetite)
- Updated Attack Trees with actual and target countermeasures
Call us today to find out how our Cyber Security professionals can help you.
or email us at